Cloudflare reveals the reason behind its 25-minute outage on 5th December

You might be aware of yesterday’s Cloudflare traffic outage; if not, then let us tell you. On December 5, 2025, at 08:47 UTC, Cloudflare experienced a significant traffic outage. The incident was resolved at 09:12 UTC, causing 25 minutes of total impact to the users. It is revealed that a subset of customers was impacted, accounting for approximately 28% of all HTTP traffic served by Cloudflare.
Cloudflare experienced a significant traffic outage on December 5, 2025, starting approximately at 8:47 UTC, for approximately 25 minutes. We are sorry for the impact that it caused to our customers and the Internet. Here's what happened: https://t.co/FTJwncz36E
— Cloudflare (@Cloudflare) December 5, 2025
The company has now revealed that this issue was not caused, directly or indirectly, by a cyber attack on Cloudflare’s systems or malicious activity of any kind. But the outage was caused due to the changes being made to Cloudflare’s body parsing logic while attempting to detect and mitigate an industry-wide vulnerability in React Server Components.
A graph is shared that shows HTTP 500 errors served by Cloudflare’s network during the incident timeframe (red line), compared to unaffected total Cloudflare traffic (green line).
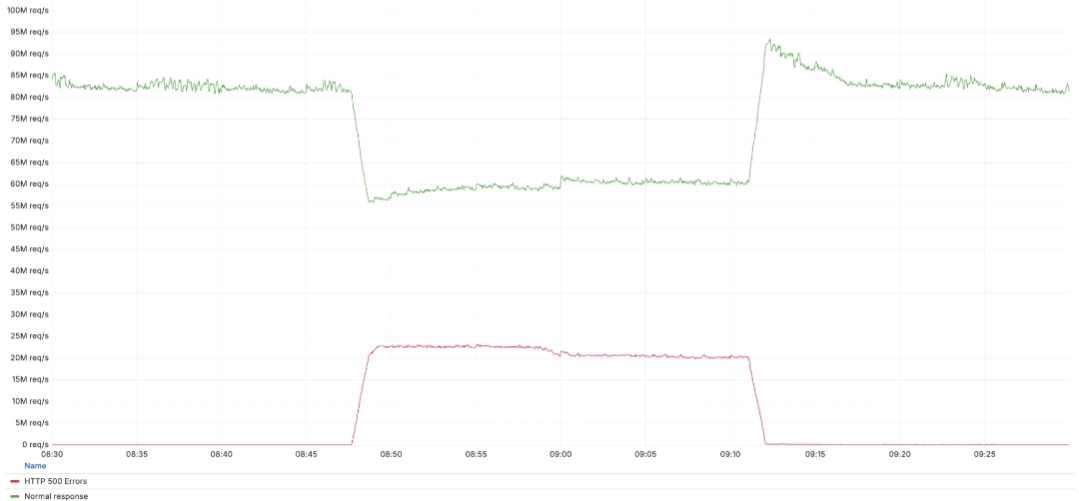
Coming to the reason. Cloudflare’s Web Application Firewall (WAF) provides customers with protection against malicious payloads. To do this, Cloudflare’s proxy buffers HTTP request body content in memory for analysis. Earlier, the buffer size was set to 128KB, but later the company started rolling out a 1MB increase in buffer size to make sure as many customers as possible were protected.
The first change was being rolled out using a gradual deployment system, but during rollout, it was noticed that Cloudflare’s internal WAF testing tool did not support the increased buffer size. Then, the second change of turning off the WAF testing tool was implemented using the global configuration system.
In Cloudflare’s FL1 version of proxy, under certain circumstances, the second change of turning off the WAF rule testing tool caused an error state that resulted in 500 HTTP error codes being served from the network. As soon as the change propagated to Cloudflare’s network, code execution in the FL1 proxy reached a bug in the rules module, resulting in HTTP code 500 errors being issued.
It is revealed that customers who have their web assets served by Cloudflare’s older FL1 proxy and had the Cloudflare Managed Ruleset deployed were impacted.
Last month, Cloudflare also experienced an outage that led to errors for nearly all of its customer base. After this incident, the company plans to make some changes, like enhanced rollouts and versioning, streamlined break-glass capabilities, and Fail-Open error handling.
Cloudflare has promised to publish details next week about the work they are doing to stop these types of incidents from occurring.


